The instructions below will show you how to hide your IP address on Mac OS X using a special type of relay server (so that websites only see the IP address of the relay). Such servers are known as proxies, and you can either use 'public' ones (free but risky), or you can use a paid service like ours. Mask ip free download - IP Scanner, Mask Pro, IP Subnet Calculator for IPv4 and IPv6, and many more programs. Display machines, Mac users, IPs on the local network. Free User rating.
-->This article is intended as a general introduction to the concepts of IP networks and subnetting. A glossary is included at the end of article.
Original product version: Windows 10 - all editions
Original KB number: 164015
Summary
When you configure the TCP/IP protocol on a Windows computer, an IP address, subnet mask, and usually a default gateway are required in the TCP/IP configuration settings.
To configure TCP/IP correctly, it is necessary to understand how TCP/IP networks are addressed and divided into networks and subnetworks.
The success of TCP/IP as the network protocol of the Internet is largely because of its ability to connect together networks of different sizes and systems of different types. These networks are arbitrarily defined into three main classes (along with a few others) that have predefined sizes, each of which can be divided into smaller subnetworks by system administrators. A subnet mask is used to divide an IP address into two parts. One part identifies the host (computer), the other part identifies the network to which it belongs. To better understand how IP addresses and subnet masks work, look at an IP (Internet Protocol) address and see how it is organized.
IP addresses: Networks and hosts
An IP address is a 32-bit number that uniquely identifies a host (computer or other device, such as a printer or router) on a TCP/IP network.
IP addresses are normally expressed in dotted-decimal format, with four numbers separated by periods, such as 192.168.123.132. To understand how subnet masks are used to distinguish between hosts, networks, and subnetworks, examine an IP address in binary notation.
For example, the dotted-decimal IP address 192.168.123.132 is (in binary notation) the 32-bit number 110000000101000111101110000100. This number may be hard to make sense of, so divide it into four parts of eight binary digits.
These eight-bit sections are known as octets. The example IP address, then, becomes 11000000.10101000.01111011.10000100. This number only makes a little more sense, so for most uses, convert the binary address into dotted-decimal format (192.168.123.132). The decimal numbers separated by periods are the octets converted from binary to decimal notation.
For a TCP/IP wide area network (WAN) to work efficiently as a collection of networks, the routers that pass packets of data between networks do not know the exact location of a host for which a packet of information is destined. Routers only know what network the host is a member of and use information stored in their route table to determine how to get the packet to the destination host's network. After the packet is delivered to the destination's network, the packet is delivered to the appropriate host.
For this process to work, an IP address has two parts. The first part of an IP address is used as a network address, the last part as a host address. If you take the example 192.168.123.132 and divide it into these two parts, you get 192.168.123. Network .132 Host or 192.168.123.0 - network address. 0.0.0.132 - host address.
Subnet mask
The second item, which is required for TCP/IP to work, is the subnet mask. The subnet mask is used by the TCP/IP protocol to determine whether a host is on the local subnet or on a remote network.
In TCP/IP, the parts of the IP address that are used as the network and host addresses are not fixed, so the network and host addresses above cannot be determined unless you have more information. This information is supplied in another 32-bit number called a subnet mask. In this example, the subnet mask is 255.255.255.0. It is not obvious what this number means unless you know that 255 in binary notation equals 11111111; so, the subnet mask is 11111111.11111111.11111111.0000000.
Lining up the IP address and the subnet mask together, the network, and host portions of the address can be separated:
11000000.10101000.01111011.10000100 -- IP address (192.168.123.132) 11111111.11111111.11111111.00000000 -- Subnet mask (255.255.255.0)
The first 24 bits (the number of ones in the subnet mask) are identified as the network address, with the last 8 bits (the number of remaining zeros in the subnet mask) identified as the host address. This gives you the following:
11000000.10101000.01111011.00000000 -- Network address (192.168.123.0) 00000000.00000000.00000000.10000100 -- Host address (000.000.000.132)
So now you know, for this example using a 255.255.255.0 subnet mask, that the network ID is 192.168.123.0, and the host address is 0.0.0.132. When a packet arrives on the 192.168.123.0 subnet (from the local subnet or a remote network), and it has a destination address of 192.168.123.132, your computer will receive it from the network and process it.
Almost all decimal subnet masks convert to binary numbers that are all ones on the left and all zeros on the right. Some other common subnet masks are:
Decimal Binary 255.255.255.192 1111111.11111111.1111111.11000000 255.255.255.224 1111111.11111111.1111111.11100000
Internet RFC 1878 (available from InterNIC-Public Information Regarding Internet Domain Name Registration Services) describes the valid subnets and subnet masks that can be used on TCP/IP networks.
Network classes
Internet addresses are allocated by the InterNIC, the organization that administers the Internet. These IP addresses are divided into classes. The most common of these are classes A, B, and C. Classes D and E exist, but are not used by end users. Each of the address classes has a different default subnet mask. You can identify the class of an IP address by looking at its first octet. Following are the ranges of Class A, B, and C Internet addresses, each with an example address:
Class A networks use a default subnet mask of 255.0.0.0 and have 0-127 as their first octet. The address 10.52.36.11 is a class A address. Its first octet is 10, which is between 1 and 126, inclusive.
Class B networks use a default subnet mask of 255.255.0.0 and have 128-191 as their first octet. The address 172.16.52.63 is a class B address. Its first octet is 172, which is between 128 and 191, inclusive.
Class C networks use a default subnet mask of 255.255.255.0 and have 192-223 as their first octet. The address 192.168.123.132 is a class C address. Its first octet is 192, which is between 192 and 223, inclusive.
In some scenarios, the default subnet mask values do not fit the needs of the organization, because of the physical topology of the network, or because the numbers of networks (or hosts) do not fit within the default subnet mask restrictions. The next section explains how networks can be divided using subnet masks.
Subnetting
A Class A, B, or C TCP/IP network can be further divided, or subnetted, by a system administrator. This becomes necessary as you reconcile the logical address scheme of the Internet (the abstract world of IP addresses and subnets) with the physical networks in use by the real world.
A system administrator who is allocated a block of IP addresses may be administering networks that are not organized in a way that easily fits these addresses. For example, you have a wide area network with 150 hosts on three networks (in different cities) that are connected by a TCP/IP router. Each of these three networks has 50 hosts. You are allocated the class C network 192.168.123.0. (For illustration, this address is actually from a range that is not allocated on the Internet.) This means that you can use the addresses 192.168.123.1 to 192.168.123.254 for your 150 hosts.
Two addresses that cannot be used in your example are 192.168.123.0 and 192.168.123.255 because binary addresses with a host portion of all ones and all zeros are invalid. The zero address is invalid because it is used to specify a network without specifying a host. The 255 address (in binary notation, a host address of all ones) is used to broadcast a message to every host on a network. Just remember that the first and last address in any network or subnet cannot be assigned to any individual host.
You should now be able to give IP addresses to 254 hosts. This works fine if all 150 computers are on a single network. However, your 150 computers are on three separate physical networks. Instead of requesting more address blocks for each network, you divide your network into subnets that enable you to use one block of addresses on multiple physical networks.
In this case, you divide your network into four subnets by using a subnet mask that makes the network address larger and the possible range of host addresses smaller. In other words, you are 'borrowing' some of the bits used for the host address, and using them for the network portion of the address. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. This works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. The first two digits of the last octet become network addresses, so you get the additional networks 00000000 (0), 01000000 (64), 10000000 (128) and 11000000 (192). (Some administrators will only use two of the subnetworks using 255.255.255.192 as a subnet mask. For more information on this topic, see RFC 1878.) In these four networks, the last 6 binary digits can be used for host addresses.
Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. These four networks would have as valid host addresses:
192.168.123.1-62 192.168.123.65-126 192.168.123.129-190 192.168.123.193-254
Remember, again, that binary host addresses with all ones or all zeros are invalid, so you cannot use addresses with the last octet of 0, 63, 64, 127, 128, 191, 192, or 255.
You can see how this works by looking at two host addresses, 192.168.123.71 and 192.168.123.133. If you used the default Class C subnet mask of 255.255.255.0, both addresses are on the 192.168.123.0 network. However, if you use the subnet mask of 255.255.255.192, they are on different networks; 192.168.123.71 is on the 192.168.123.64 network, 192.168.123.133 is on the 192.168.123.128 network.
Default gateways

If a TCP/IP computer needs to communicate with a host on another network, it will usually communicate through a device called a router. In TCP/IP terms, a router that is specified on a host, which links the host's subnet to other networks, is called a default gateway. This section explains how TCP/IP determines whether or not to send packets to its default gateway to reach another computer or device on the network.
When a host attempts to communicate with another device using TCP/IP, it performs a comparison process using the defined subnet mask and the destination IP address versus the subnet mask and its own IP address. The result of this comparison tells the computer whether the destination is a local host or a remote host.
If the result of this process determines the destination to be a local host, then the computer will send the packet on the local subnet. If the result of the comparison determines the destination to be a remote host, then the computer will forward the packet to the default gateway defined in its TCP/IP properties. It is then the responsibility of the router to forward the packet to the correct subnet.
Troubleshooting
TCP/IP network problems are often caused by incorrect configuration of the three main entries in a computer's TCP/IP properties. By understanding how errors in TCP/IP configuration affect network operations, you can solve many common TCP/IP problems.
Incorrect Subnet Mask: If a network uses a subnet mask other than the default mask for its address class, and a client is still configured with the default subnet mask for the address class, communication will fail to some nearby networks but not to distant ones. As an example, if you create four subnets (such as in the subnetting example) but use the incorrect subnet mask of 255.255.255.0 in your TCP/IP configuration, hosts will not be able to determine that some computers are on different subnets than their own. When this happens, packets destined for hosts on different physical networks that are part of the same Class C address will not be sent to a default gateway for delivery. A common symptom of this is when a computer can communicate with hosts that are on its local network and can talk to all remote networks except those that are nearby and have the same class A, B, or C address. To fix this problem, just enter the correct subnet mask in the TCP/IP configuration for that host.
Incorrect IP Address: If you put computers with IP addresses that should be on separate subnets on a local network with each other, they will not be able to communicate. They will try to send packets to each other through a router that will not be able to forward them correctly. A symptom of this problem is a computer that can talk to hosts on remote networks, but cannot communicate with some or all computers on their local network. To correct this problem, make sure all computers on the same physical network have IP addresses on the same IP subnet. If you run out of IP addresses on a single network segment, there are solutions that go beyond the scope of this article.
Incorrect Default Gateway: A computer configured with an incorrect default gateway will be able to communicate with hosts on its own network segment, but will fail to communicate with hosts on some or all remote networks. If a single physical network has more than one router, and the wrong router is configured as a default gateway, a host will be able to communicate with some remote networks, but not others. This problem is common if an organization has a router to an internal TCP/IP network and another router connected to the Internet.
References
Two popular references on TCP/IP are:
- 'TCP/IP Illustrated, Volume 1: The Protocols,' Richard Stevens, Addison Wesley, 1994
- 'Internetworking with TCP/IP, Volume 1: Principles, Protocols, and Architecture,' Douglas E. Comer, Prentice Hall, 1995
It is recommended that a system administrator responsible for TCP/IP networks have at least one of these references available.
Glossary
Broadcast address--An IP address with a host portion that is all ones.
Host--A computer or other device on a TCP/IP network.
Internet--The global collection of networks that are connected together and share a common range of IP addresses.
InterNIC--The organization responsible for administration of IP addresses on the Internet.
IP--The network protocol used for sending network packets over a TCP/IP network or the Internet.
IP Address--A unique 32-bit address for a host on a TCP/IP network or internetwork.
Network--There are two uses of the term network in this article. One is a group of computers on a single physical network segment; the other is an IP network address range that is allocated by a system administrator.
Network address--An IP address with a host portion that is all zeros.
Octet--An 8-bit number, 4 of which comprise a 32-bit IP address. They have a range of 00000000-11111111 that correspond to the decimal values 0- 255.
Packet--A unit of data passed over a TCP/IP network or wide area network.
RFC (Request for Comment)--A document used to define standards on the Internet.
Router--A device that passes network traffic between different IP networks.
Subnet Mask--A 32-bit number used to distinguish the network and host portions of an IP address.
Subnet or Subnetwork--A smaller network created by dividing a larger network into equal parts.
TCP/IP--Used broadly, the set of protocols, standards, and utilities commonly used on the Internet and large networks.
Wide area network (WAN)--A large network that is a collection of smaller networks separated by routers. The Internet is an example of a large WAN.
Looking to hide your IP address and want to learn how to hide your IP address on your mac? Although you can never fully hide it, you can take precautions to change or disguise it using a variety of techniques. This article will be covering a lot of methods to cover your IP address on your Mac, and also give you the pros and cons of each method.
Mask Ip For Mac Shortcut
But this doesn’t exist. Any method of hiding IP addresses is not ‘Mac-exclusive’, rather, these methods have universal application.
Make sure to read till the end because that’s where we put the easiest choice!
What is an IP address?
Now before we start to cover up IPs, what are they? IP addresses are, as they say, addresses, but for each of your devices which can connect to the internet. It basically differentiates between devices across the internet, and I guess you do not be muddled and be confused for some other device or for someone else.
This is what an IP address looks like:
Now this IP address is what the server recognizes your device by. This is an IPv4, meaning it has 4 parts to it. But there are IPv6 versions, which have 6 parts to their IP address, and are intended for high personnel and made public when we run out of v4 versions.
Now, hiding your IP address provides you defense against all kinds of attacks, ranging from man-in-the-middle attacks, to also bouncing off signals to prevent you from being detected. But for the general public, it’s nothing more but a privacy measure to prevent attacks. Now, let’s do some hiding.
Fair warning: Some of these methods are dangerous and are not the best thing to do to your internet connection, I will mention the ones that are dangerous.
Method One: Use a VPN
This is by far the most useful and safest of all the ways to hide IPs.
A VPN or a Virtual Private Network is an exclusive network with added protection which can also allow you to go across countries and act as a device from your desired location by using proxies. Oyun for mac.
Mask Ip Mac
Does work for all computers which have access to that VPN. Not only are you changing IP addresses, but you may also change your apparent location, giving you access to content that is banned or not available in your country. The most recommended VPN for the job would be ExpressVPN, but there are other VPNs that can do the same thing. Some VPNs come with antivirus packages which also include convenient features like Mac adware removal.
Now how you change it depends on the VPN you’re using. A VPN will automatically change your IP address as soon as you use it, and proxies can get your location masked. The only downside to this method is the fact that you need to pay for these VPNs on a monthly basis, and they might weigh down on your pocket and are mostly unnecessary for people who rarely surf the web, and are meant for those who really want to watch content from other countries and want some extra security.
Mask My Ip For Mac
The best free VPN for Mac use should be chosen accordingly with the right type of program in mind. You have many choices to use when getting a VPN ready, but you need to look at how you’re going to make the most out of your content. The best VPN for Mac will be something that protects you while online and ensures you don’t have your data stolen. You should have a solution that keeps your content secure, so nothing wrong develops on your computer. Be aware of what’s around, but don’t forget to see the terms of the free VPN options out there. You might find that there’s plenty of things to like about the VPN world, especially if you want to take advantage of what your Mojave-powered Apple computer can handle for your desires.
Some best VPNs are Tunnel Bear (free and paid), ExpressVPN, NordVPN, Hotspot Shield (free and paid) etc. according to Upside Down Blogger.
Method 2: Use a Proxy
Now if you are not that concerned about your security and want some basic protection for your IP address, you could use some proxies. VPNs too are technically proxies, but here they mean an SSL or SSH proxy. They are able to protect your IP address, but they also do not provide the additional security provided by VPNs. They also are not able to protect you from some higher-security DNS servers, which can still have access to your real IP address. They are still prone to some man-in-the-middle attacks.
But they are free, so you still save money for a little less protection. There are also browser extensions that can act and give you the power of proxies, and they perform decently but are still not going to protect you from all attacks.
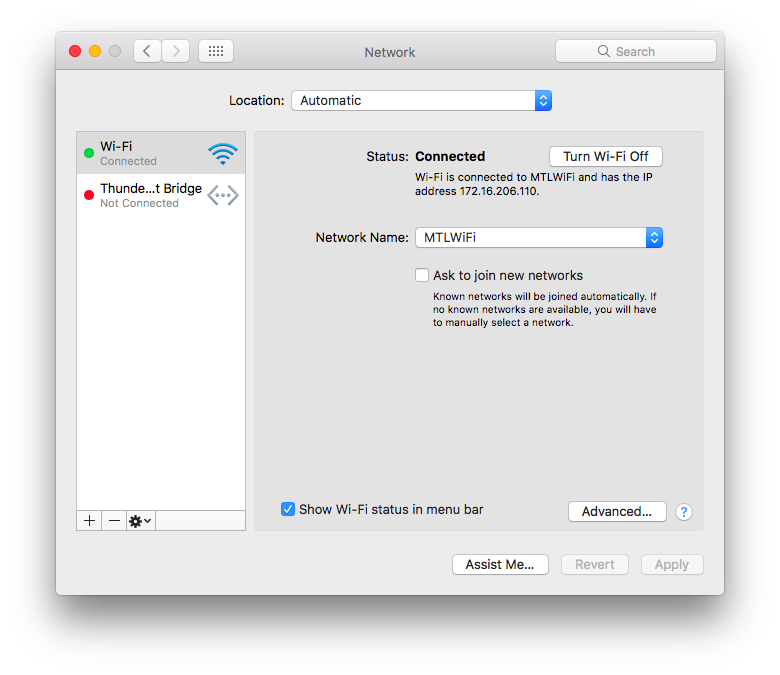
Enter proxy server settings on Mac
If your computer is connected to a local network that’s protected from the internet by a firewall, you may need to specify proxy servers or use the FTP passive mode (PASV) to access some internet sites. A proxy server is a computer on a local network that acts as an intermediary between a single computer user and the internet so that the network can ensure security, administrative control, and caching service.
How enter proxy server settings on Mac:
- On your Mac, choose Apple menu > System Preferences, then click Network.
- Select the network service you use in the list — for example, Ethernet or Wi-Fi.
- Click Advanced, then click Proxies.
- If you configure your proxy server settings automatically, select Auto Proxy Discovery to automatically discover proxy servers, or select Automatic Proxy Configuration if you’re using a proxy auto-configuration (PAC) file. If you select Automatic Proxy Configuration, enter the address of the PAC file in the URL field. Check with your network administrator if you need more information.
- If you configure your proxy settings manually, do the following:
- Select a proxy server, such as FTP Proxy, then type its address and port number in the fields on the right.
- Select the “Proxy server requires password” tickbox if the proxy server is protected by a password. Enter your account name and password in the Username and Password fields.
Some proxies are paid, but there are also relatively safe free ones.
Method 3: Change your network
I think I do not need to explain this, but I will anyway. Your network determines the IP address of your computer or device, and changing the network router can help you for some time when your IP is compromised. You could probably run a hotspot on your mobile, and it will cover your internet needs for some time. The downside of this method is that we cannot use this for heavy use, and it too can only help you for some time until this too is compromised.
This method of hiding your IP address is also very easy, but probably not one of the options with the current situations in the world. It’s just a valid method and is great for overall internet security.
Method 4: Use Tor (A web browser )
Tor is a web browser which is the most secure ones out there. Originally designed for the US military and intelligence services, it has now been passed onto the public for more anonymity for the government. You could trust the US military to keep your privacy safe, at least for themselves, but you could stumble upon the dark web, which is accessed via .onion sites, which house all sorts of illegal activities, from drug trafficking to hitmen hiring services. So be careful while roaming around Tor.
Method 5: Ask your ISP (Internet Service Provider ) to change it for You
If you have a friendly ISP then this is probably the best way, just ask them to do it for you! sit back and relax!
You can do this on your Mac itself, by going to your TCP/IP settings and asking for a new DHCP lease, which will give you a new IP address which is private. Or to change the IP of your entire network, you can ask your ISP to change your ISP for you if your current IP is compromised.
But remember one thing, you cannot hide your IP from your ISP. So if that’s your aim, you could stop trying.
Mask Ip Address Mac
Anyways, I hope you found this article helpful. Thank you for sticking around until the end of the post.
